Why is CSPM so important?
Gartner predicts that 50% of enterprises will adopt the multi cloud strategy by 2025. According to relevant reports released by IDC Consulting, 50% of Chinese enterprise applications will be deployed in a containerized hybrid cloud/multi-cloud environment to provide an agile, seamless deployment and management experience by 2023. In "China Cloud Survey 2021", McKinsey also points out that the Chinese cloud market will show a trend of hybrid and multi-cloud. As cloud architectures become increasingly complex, it is difficult for security personnel to either identify which of the thousands of configuration options offered by different cloud providers poses risks, or ensure that consistent security policies are implemented across different clouds. Any configuration error may lead to sensitive data leakage and escalation into a serious security issue, posing significant risks in legal and financial aspects.
CSPM applies best security practices to hybrid cloud and multi cloud environment in a unified interface, identifies and fixes security problems in complex cloud environments automatically, and protects cloud infrastructure and cloud data security.
Product introduction
Product advantages
Less operational costs and complexity
No installation of security agents is required, avoiding complex compatibility issues completely.
Remain the same operation habits in a unified WEB interface to manage the security of multiple public clouds and Hybrid cloud, without logging into the security interfaces of different cloud providers for completely different operations.
Quick deployment within a few minutes
One AKSK or STS credential with read-only permission at minimum is required to easily connect to the cloud providers to accomplish all functions, without the long-term data accumulation or cumbersome configuration. The effect can be seen within five minutes.
The fully automated workflow without affecting business delivery speed
It can integrate with mainstream DevOps platforms to automatically discover cloud resource security issues before the production phase during the development process, ensuring timely and secure delivery of business.
No Intrusiveness to the business and no impact on infrastructure or business stability
Retrieve cloud resources and configuration policies with standard APIs provided by cloud providers without scanning any cloud infrastructure or business systems, nor affecting stability anywhere.
Product features
- Overall visibility
across multi-cloud env - Protect cloud data security
- Continuous cloud compliance
- Cloud identity privilege management
- Cloud intrusion detection response
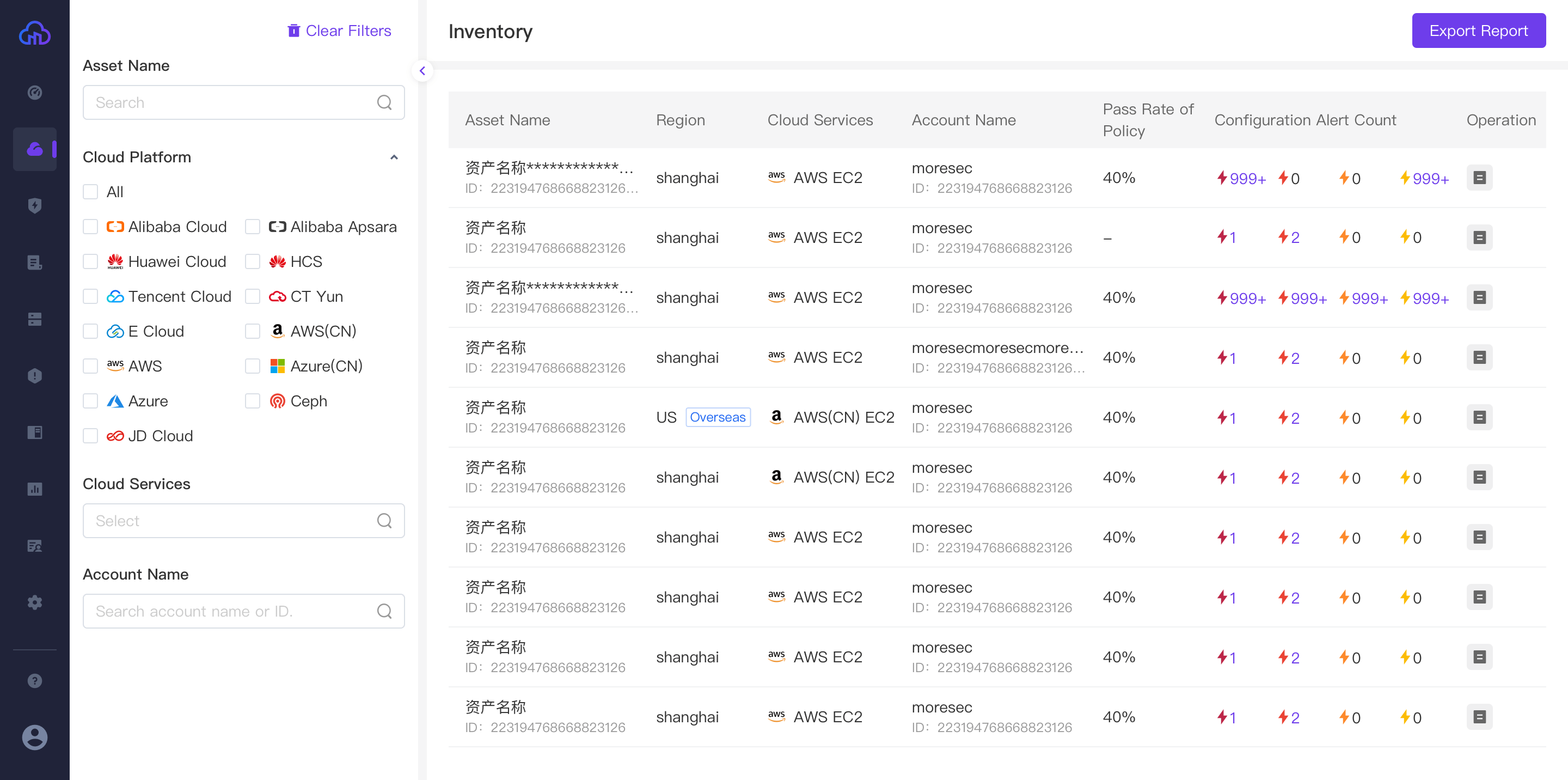
- Asset List: Connect all cloud platforms through the API of cloud providers, and help discover, identify, and manage cloud assets automatically. Asset models shall be established and asset status shall be updated continuously to solve the problem of unified asset management in multi cloud environments.
- Advanced Asset Management: Merge multiple cloud services with similar functions through abstract logic and provide advanced query statement. It is more convenient to manage cloud assets scattered around based on business roles.
- Comprehensive and extensive support from cloud service providers.